010Editor注册流程分析
无限试用:
1
| rm -rf ~/.config/SweetScape/010\ Editor.ini
|
key
1
2
| Name: Forgo7ten
License: 1f93-56ac-c63e-540d-a9ab
|
注册完后
Linux:chattr +i 010\ Editor.ini
Mac:chflags uchg 010\ Editor.ini
Version: 12.0.1
分析
通过查找相应字符串"Invalid name or password"定位到关键函数
Verify函数

大概流程为
可以发现h157和h158行调用的函数至关重要。
下面的switch是判断其返回值,如果返回值verify_b == 0xDB时,注册成功
verify_mothod_函数
其中verify_b = verify_mothod_(qword_7FF7DB0EEE50, 13i64, 18887i64);如下

发现还是通过调用verify_mothod函数的返回值来判断的
verify_mothod函数

执行流程:
-
h48:判断用户名和密码均不为空,开始执行
-
通过h50: encode_password(a1, en_password);函数,将每两位密码合并成一个字节,得到一个长度为10的字节数组(TimeLicense Key) [或者长度为8的字节数组]
-
h51-h59:判断用户名不能等于999
-
h60-h94:
- 用户名前两个字符如果为
"Cow",加密后的password不能为[0xC4, 0x4A, 0x55, 0x59, 0x2A, 0x35, 0xE2, 0xC4, 0x65, 0xAC]
- 用户名前两个字符如果为
"JUY",加密后的password不能为某个数组(有些元素为空)
- 貌似没什么用
-
h95-h100:简单的将编码后的密码数组赋值给变量
-
h101-h184:
-
这里是对三种license类型的判断。
9c Evaluation Key
fc VersionLicense Key
ac TimeLicense Key
-
重点分析0xac,时间许可证
-
首先根据en_password的[1][2][5][7]下标通过get_count函数解析出授权次数count
其中传入的参数低字节为[5]^[2],高字节为[7]^[1]
然后判断count <=1000,处于[1,1000]才有效
-
然后通过get_days函数解析出过期天数days
传入的第一个参数也同理,三个字节从低到高分别为0^6 4^8 5^9
-
之后跳转到LABEL_26,然后通过用户名计算出4 5 6 7下标的字节数组,然后比较,需要相同
-
h124-h146不进入。h147-h155,在这里如果days存在,并且数值大于0x49c7的话,转到成功返回值0x2D
encode_password函数

因为没有用循环来写,看着有些长,但实际上操作还是很简单的
执行流程:
- h50-h51:判断password的长度,若不等于19或者24,退出
- h52-h62:判断password格式,
-是不是在各自的位置(4 9 14 19)
- h69-h152:除去
-,每两个字符合并到一起,首先通过cast_num函数得到相应的数字,最终得到的数字为16*[i]+[i+1];除去-还有20个字符,两两组合得到一个长度为10的char数组
cast_num函数

将数字0-9转换为0-9,字母不论大小写a-z对应着10-35
get_count

变换比较简单,即count = (((((p5 ^ p2) + ((p7 ^ p1) << 8)) ^ 0x7892) + 0x4D30) ^ 0x3421 )/0xB
其中要正好能被0xb整除,相应的逆过来就是
((p5 ^ p2) + ((p7 ^ p1) << 8)) = count *0xb ^0x3421 - 0x4d30 ^ 0x7892
get_days

逆运算为
en_password[6] ^ p0) + ((p5 ^ en_password[9]) << 16) + ((en_password[8] ^ en_password[4]) << 8 = a1 = * 0x11) ^ 0xFFE53167) + 0x2C175)) ^ 0x22C078 ^ 0x5B8C27)
get_pwd_by_name函数

通过用户名、授权数量、到期时间来生成password中的4位,然后进行校验。
注册机编写
爆破
old
整个是通过判断verify_mothod函数的返回值来验证的。可以直接修改该函数的返回值。
为了不影响程序的运行逻辑,我选择了一条程序存在的路径,同时也是最简单的一条。直接在h48,改成强制跳转跳过if语句体,然后将原本的返回值修改为0x2D。

这样即实现了随意输入(不能为空,判断空的逻辑在verify函数中)便可以注册了。更不会有弹窗了,但感觉不是很完美。
有效爆破
相关patch地址:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
| version:12.0.1
IDA修改base:0x0
---------------------------------------
① 核心校验注册码
.text:000000000034A32A jmp loc_34A619 ; Keypatch modified this from:
.text:000000000034A32A ; jz loc_34A619
.text:000000000034A32A ; Keypatch padded NOP to next boundary: 1 bytes
.text:000000000034A619 mov eax, 2Dh ; '-' ; Keypatch modified this from:
.text:000000000034A619 ; mov eax, 93h
---------------------------------------
② 次要核心校验注册码
.text:000000000034AD83 jmp loc_34AE63 ; Keypatch modified this from:
.text:000000000034AD83 ; jz short loc_34AD95
.text:000000000034AD83 ; mov eax, 113h
.text:000000000034AD83 ; Keypatch padded NOP to next boundary: 2 bytes
----------------------------------------
③ 网络验证函数返回1
.text:00000000001F7754 jmp loc_1F7E35 ; Keypatch modified this from:
.text:00000000001F7754 ; jz loc_1F7E35
.text:00000000001F7754 ; Keypatch padded NOP to next boundary: 1 bytes
.text:00000000001F7E35 mov eax, 1 ; Keypatch modified this from:
.text:00000000001F7E35 ; mov eax, 0FFFFFFFFh
去掉(EXPIRED)提示(非必要)
.text:00000000001F567D jmp short loc_1F5690 ; Keypatch modified this from:
.text:00000000001F567D ; jns short loc_1F5690
---------------------------------------
Single User License
.text:00000000001F5F53 jmp short loc_1F5F66 ; Keypatch modified this from:
.text:00000000001F5F53 ; jnz loc_1F60B1
.text:00000000001F5F53 ; Keypatch padded NOP to next boundary: 4 bytes
Single User
.text:000000000034B173 nop ; Keypatch modified this from:
.text:000000000034B173 ; jnz loc_34B2C2
.text:000000000034B173 ; Keypatch padded NOP to next boundary: 5 bytes
.text:000000000034B174 nop
.text:000000000034B175 nop
.text:000000000034B176 nop
.text:000000000034B177 nop
.text:000000000034B178 nop
Single User(非必要)
.text:000000000034B1DF nop ; Keypatch modified this from:
.text:000000000034B1DF ; jnz short loc_34B1FC
.text:000000000034B1DF ; Keypatch padded NOP to next boundary: 1 bytes
.text:000000000034B1E0 nop
---------------------------------------
感觉没必要
无法连接服务器(③控制)
.text:00000000001F547A jmp loc_1F5575 ; Keypatch modified this from:
.text:00000000001F547A ; jns loc_1F554A
.text:00000000001F547A ; Keypatch padded NOP to next boundary: 1 bytes
注册码已封禁(③控制)
.text:00000000001F554A jmp short loc_1F5575 ; Keypatch modified this from:
.text:00000000001F554A ; jnz short loc_1F5575
注册函数(②控制)
.text:00000000001F559B nop ; Keypatch modified this from:
.text:00000000001F559B ; jnz loc_1F5731
.text:00000000001F559B ; Keypatch padded NOP to next boundary: 5 bytes
.text:00000000001F559C nop
.text:00000000001F559D nop
.text:00000000001F559E nop
.text:00000000001F559F nop
.text:00000000001F55A0 nop
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
| version:13.0
IDA修改base:0x0
---------------------------------------
①核心校验注册码
.text:000000000036E32A jmp loc_36E657 ; Keypatch modified this from:
.text:000000000036E32A ; jz loc_36E657
.text:000000000036E32A ; Keypatch padded NOP to next boundary: 1 bytes
.text:000000000036E657 mov eax, 2Dh ; '-' ; Keypatch modified this from:
.text:000000000036E657 ; mov eax, 93h
---------------------------------------
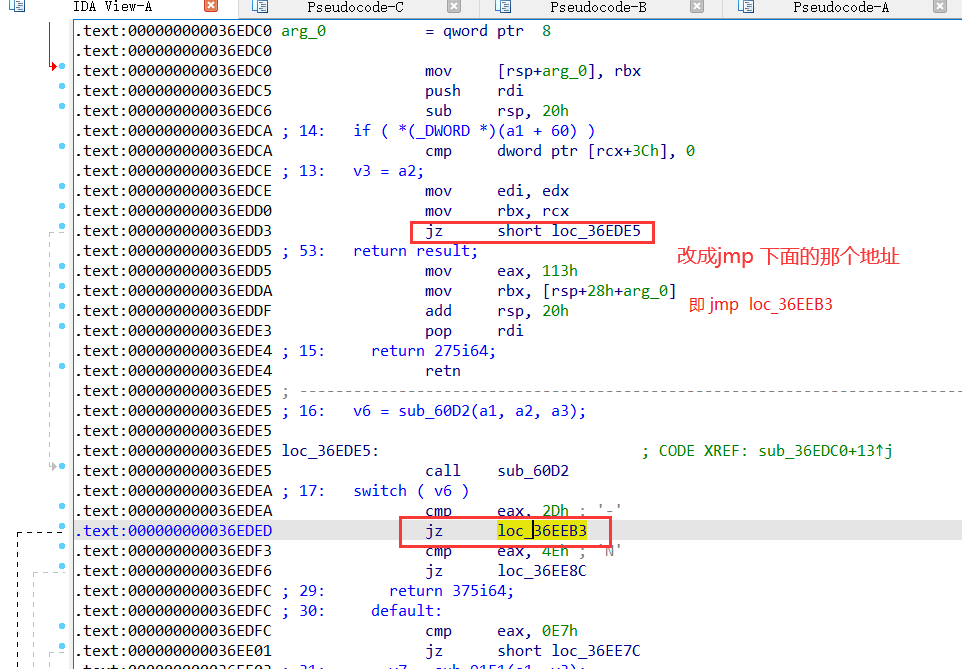
②次要核心校验注册码
.text:000000000036EDD3 jmp loc_36EEB3 ; Keypatch modified this from:
.text:000000000036EDD3 ; jz short loc_36EDE5
.text:000000000036EDD3 ; mov eax, 113h
.text:000000000036EDD3 ; Keypatch padded NOP to next boundary: 2 bytes
---------------------------------------
③ 网络验证函数返回1
.text:0000000000212984 jmp loc_213055 ; Keypatch modified this from:
.text:0000000000212984 ; jz loc_213055
.text:0000000000212984 ; Keypatch padded NOP to next boundary: 1 bytes
.text:0000000000213055 mov eax, 1 ; Keypatch modified this from:
.text:0000000000213055 ; mov eax, 0FFFFFFFFh
---------------------------------------
③ 美观:去除(EXPIRED)提示
.text:00000000002108AD jmp short loc_2108C0 ; Keypatch modified this from:
.text:00000000002108AD ; jns short loc_2108C0
---------------------------------------
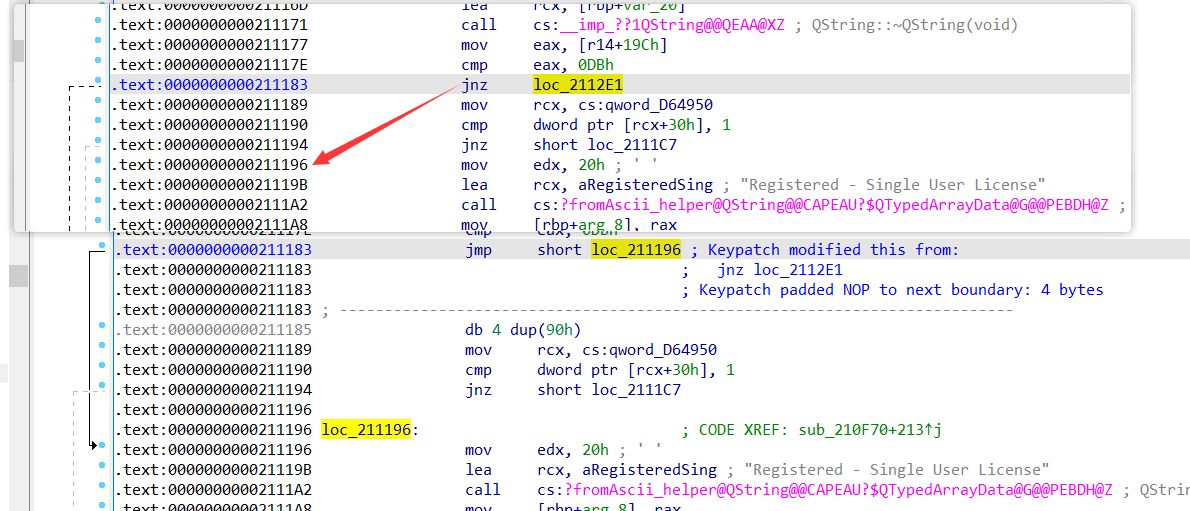
④ 美观:修改Single User License
.text:0000000000211183 jmp short loc_211196 ; Keypatch modified this from:
.text:0000000000211183 ; jnz loc_2112E1
.text:0000000000211183 ; Keypatch padded NOP to next boundary: 4 bytes
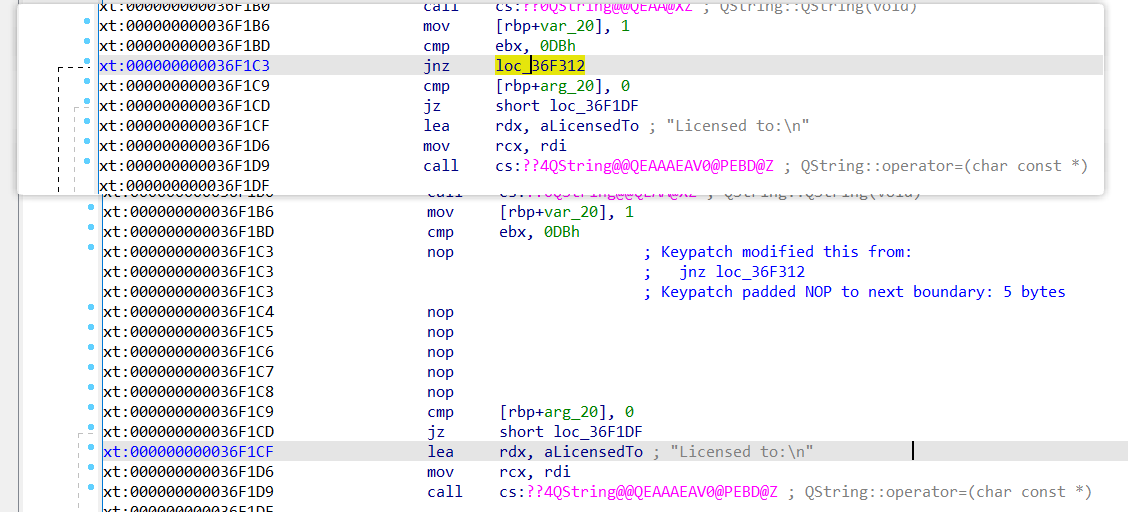
.text:000000000036F1C3 nop ; Keypatch modified this from:
.text:000000000036F1C3 ; jnz loc_36F312
.text:000000000036F1C3 ; Keypatch padded NOP to next boundary: 5 bytes
.text:000000000036F1C4 nop
.text:000000000036F22F nop ; Keypatch modified this from:
.text:000000000036F22F ; jnz short loc_36F24C
.text:000000000036F22F ; Keypatch padded NOP to next boundary: 1 bytes
---------------------------------------
Address Length Original bytes Patched bytes
00000000002108AD 0x1 79 EB
0000000000211183 0x6 0F 85 58 01 00 00 EB 11 90 90 90 90
0000000000212984 0x4 0F 84 CB 06 E9 CC 06 00
0000000000212989 0x1 00 90
0000000000213056 0x4 FF FF FF FF 01 00 00 00
000000000036E32A 0x4 0F 84 27 03 E9 28 03 00
000000000036E32F 0x1 00 90
000000000036E658 0x1 93 2D
000000000036EDD3 0x7 74 10 B8 13 01 00 00 E9 DB 00 00 00 90 90
000000000036F22F 0x2 75 1B 90 90
000000000066CD8E 0x2 73 65 67 00
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
| version:13.0.1
IDA修改base:0x0
---------------------------------------
①核心校验注册码
.text:000000000036E50A jmp loc_36E837 ; Keypatch modified this from:
.text:000000000036E50A ; jz loc_36E837
.text:000000000036E50A ; Keypatch padded NOP to next boundary: 1 bytes
.text:000000000036E837 mov eax, 2Dh ; '-' ; Keypatch modified this from:
.text:000000000036E837 ; mov eax, 93h
---------------------------------------
②次要核心校验注册码
.text:000000000036EFB3 jmp loc_36F093 ; Keypatch modified this from:
.text:000000000036EFB3 ; jz short loc_36EFC5
.text:000000000036EFB3 ; mov eax, 113h
.text:000000000036EFB3 ; Keypatch padded NOP to next boundary: 2 bytes
---------------------------------------
③ 网络验证函数返回1
.text:0000000000212B44 jmp loc_213215 ; Keypatch modified this from:
.text:0000000000212B44 ; jz loc_213215
.text:0000000000212B44 ; Keypatch padded NOP to next boundary: 1 bytes
.text:0000000000213215 mov eax, 1 ; Keypatch modified this from:
.text:0000000000213215 ; mov eax, 0FFFFFFFFh
---------------------------------------
③ 美观:去除(EXPIRED)提示
.text:0000000000210A6D jmp short loc_210A80 ; Keypatch modified this from:
.text:0000000000210A6D ; jns short loc_210A80
---------------------------------------
④ 美观:修改Single User License
.text:0000000000211343 jnz short loc_211356 ; Keypatch modified this from:
.text:0000000000211343 ; jnz loc_2114A1
.text:0000000000211343 ; Keypatch padded NOP to next boundary: 4 bytes
.text:000000000036F3A3 nop ; Keypatch modified this from:
.text:000000000036F3A3 ; jnz loc_36F4F2
.text:000000000036F3A3 ; Keypatch padded NOP to next boundary: 5 bytes
.text:000000000036F40F nop ; Keypatch modified this from:
.text:000000000036F40F ; jnz short loc_36F42C
.text:000000000036F40F ; Keypatch padded NOP to next boundary: 1 bytes
---------------------------------------
Address Length Original bytes Patched bytes
0000000000210A6D 0x1 79 EB
0000000000211343 0x6 0F 85 58 01 00 00 75 11 90 90 90 90
0000000000212B44 0x4 0F 84 CB 06 E9 CC 06 00
0000000000212B49 0x1 00 90
0000000000213216 0x4 FF FF FF FF 01 00 00 00
000000000036E50A 0x4 0F 84 27 03 E9 28 03 00
000000000036E50F 0x1 00 90
000000000036E838 0x1 93 2D
000000000036EFB3 0x7 74 10 B8 13 01 00 00 E9 DB 00 00 00 90 90
000000000036F3A3 0x6 0F 85 49 01 00 00 90 90 90 90 90 90
000000000036F40F 0x2 75 1B 90 90
|
爆破思路
首先定位Invalid name or password. Please enter your name and password exactly as given when you purchased 010 Edit字符串所在的函数A
-
核心校验注册码
函数A中,找如下代码

进入圈起来的这个函数,修改下图圈起来的跳转为jmp

跳转的地址,改为mov eax,2Dh;也就是修改该函数的返回值为45
-
次要核心校验注册码
函数A中,找到如下函数

修改该函数返回值为219 仅改这一处即可


-
网络验证函数返回1
同样是函数A的如下代码

第一步

jmp跳转过去的地址,改为1

-
美观:去除(EXPIRED)提示
在函数A的如下代码中,改成jmp

-
美观:修改SingleUserLicense
-
修改注册窗口的字符串
搜索字符串Registered - Single User License,修改跳转跳到这里

-
修改其余
搜索字符串Licensed to:\n

在不远的下方有一个Single,将跳转nop掉